Four months ago I moved my last remaining domain away from Moniker.
The timing was apparently right, as today I received notifications of a forced password reset via email.
While these emails were legitimately sent out, they ended up in my spam folder, which does not reflect positively on Moniker’s reputation. The mail out relay came from 109.234.108.151 which is a Key Systems IP.
Both emails contained my account credentials, the account number and a new password, along with an explanation on why the changes are made, and I quote:
“With the recent ShellShock vulnerability making headlines in addition to the numerous instances of security breaches around the world each week, security is an ever increasing concern. We also saw an increased attempt to access Moniker accounts by brute force attacks.”
The first major security faux pas of this forced password reset is that the email – an insecure, open text protocol – contains sensitive account information. Without any encryption, the account credentials traveled across various routes on the Internet, open for anyone along the way with a packet sniffer to process them.
After logging in to my account I examined my IP access log, which shows an IP in the UK successfully logging in as below:
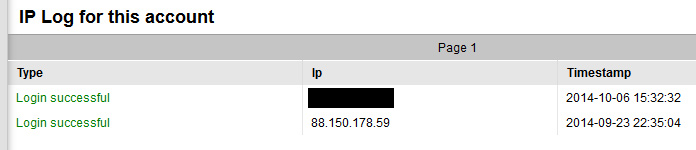
A secondary account at Moniker displayed the following IP log:
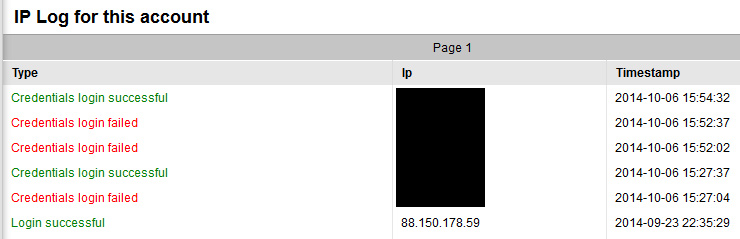
The failed attempts above are actually mine, after I struggled a bit with the newly issued credentials. However, the IP that successfully logged in into both accounts on 9/23/2014 is not me, but rather, a server hosted in the UK.
I have not visited that IP directly, and it appears to be running both a web server and a VPN, both of which indicate a rogue system that successfully accessed both of my Moniker accounts two weeks ago. While the so-called “ShellShock bug” was publicly announced on 9/24, the exploit was quite possibly shared on “zero day” forums attempting to utilize security flaws in operating systems or other software, earlier.
The consequences of this apparent mass breach can be summarized as such: Change all your passwords across any medium that might have shared them with your Moniker account.
Additionally, I don’t believe anyone with a basic amount of sanity left, would carry on using Moniker as a domain registrar.

In checking my ip log I have the same ip showing 88.150.178.59:
2014-09-23 22:25:28
I would like to hear from Moniker.com who did this?
James – I believe that the breach involved access to a list of customer account credentials at Moniker, that were then “tested out” for validity and/or automated extraction of account information, by whoever operates the IP above.
Thanks, it would be nice if Moniker.com commented on this.
Make sure when you change your password at Moniker that you Verify and Save it.
The first time I only Verified it and didn’t SAVE. Normally on a password change you simply click the SAVE button or confirm etc… but at Moniker you have to click the button to the right, which is Verify. Then you have to click the same button again, which switches to SAVE.
BTW, I also had the same IP Address log into my account:
88.150.178.59 2014-09-23 22:38:50
Also on a secondary account which shows a new and earlier date of September 20 2014:
88.150.178.59 2014-09-20 09:01:54
I wish Moniker would comment on this, we now have three people who identified the same unauthorized logon from the same ip! I am sure if others here looked they would see the same thing.
Moniker sent me the account number and reset password for a complete strangers account in this fiasco.
Good job I’m honest.
Same IP entered also in my account, but I transferred out all my domains from Moniker months ago, anyway why even domains transferred from moniker to network solutions are using the same moniker’s privacy service? It sounds a little bit strange to me…
There are now reports of several domains stolen from Moniker accounts between 9/22 and 10/3 that may be related to the incident. One of the parties requested that the domains don’t get publicized.
The wonderful new and improved Moniker system does not even notify you of a push for outgoing or incoming domains! In addition the same is not logged in transaction history. I think that would be important…
The same IP logged into my account:
88.150.178.59 2014-09-23 15:15:33
88.150.178.59 2014-09-21 17:00:39
What is even worse… Moniker deleted everyone’s account history, invoices etc… prior to May 31, 2014.
Moniker is changing it’s name to Stupid. I wonder how long before Moniker goes under?
I can’t transfer them out quick enough, takes a bloody week, uniregistry has been very good, like the point, and click platform.
Fantastic!
Moniker won’t allow me to change my own password now. I get the following error message:
“This option is only available for the main user of this account.”
Two of my accounts were accessed from:
88.150.178.59
9-24-2014
One of those accounts was also accessed from:
199.59.62.125
9-28-2014
Location: Tulsa, Oklahoma
ISP: Hostwinds LLC
No domains are missing. Checking the lock status now.
I have been moving domains out for about two months; more to do.
I theorize that the thieves must have been able to see the list of domains contained within each account, before they logged in to a given account.
One of my accounts has low-value domains in it, and that is the only account they did not access.
It happened to me, too!
Login successful 88.150.178.59 2014-09-18 14:11:23
all the way back on Thursday, September 18th! However, the hacker took a look around, and said, “Let’s blow this popsicle stand,” because my domains are not high value . . .
@ Joseph, Chris called me back from Moniker, and led me how to do it. Your user name might not work – try your main (new) account number as a login. What I did was change psswd for sub-account from Manage Account Users on the left. Then I logged out, and tested the new psswd for that account, and logged back in and changed the psswd for the main account.
@ David said[blockquote]I theorize that the thieves must have been able to see the list of domains contained within each account, before they logged in to a given account.
One of my accounts has low-value domains in it, and that is the only account they did not access.[/blockquote]Interesting thought!
@David,
I had an account with zero domains in it and they logged in, so not likely that they could see what domains were in what account.
I have no proof, but I think the other criteria the thieves used (in addition to higher-value targets), after they logged-in to a Moniker account, was to find internal Moniker account e-mail addresses that were easily exploitable, such as an e-mail account that was using the same or similar password as the Moniker account (which they already knew).
I think they knew they were working on a short time-frame until the server exploit was patched, and did not want to take much time hacking difficult e-mail addresses. Go for the domains that can be transferred the quickest.
They had to be able to access the internal Moniker account e-mail address before initiating a transfer, so that the Moniker account holder would not realize what was happening.
Without proof, I could well be wrong, but this scenario seems possible.
Regardless, it seems a good idea to host your internal e-mail addess away from the registrar, and use a different password than the registrar account. Also, do not use that internal domain for your public WhoIs.
@Jamie Zoch:
Thank you for the information.
Regardless of how they gained access to the user accounts and their respective passwords, the thieves most likely logged into every single account by running a script. That’s why the same IP is identified accessing the accounts, successfully logging in without any failures.
Most likely, the script swiped and stored a list of domains from every account that was accessed, along with other info, compiling a list. Then, they processed that list to identify valuable domains and targeted the holding accounts, pushing domains elsewhere or transferring them away from Moniker.
It’s a major clusterfuck.
Inside job????
Nowadays gmail and google apps email accounts support 2-factor authentication, where you need to type in a 6 digit number that is sent to your phone via SMS as well as your password in order to log in. I suggest using an email with 2-factor authentication for your contact info.
Also, Moniker have repeatedly proved themselves as incompetent, so use another registrar with a proven track record such as Fabulous, Dynadot or Godaddy.
I would be interested to hear from the people who had their domains stolen, about how exactly it happened. It seems like an important fact as to whether the thieves hacked into the owner’s email account to approve the domain transfer, or if the transfer was somehow approved internally at Moniker.com, bypassing the email notification/verification part.
Also, in regards to what Jamie Zoch said about the Verify/Save buttons at Moniker, their system is totally insane with that part. I use Moniker.com all the time and still frequently make that mistake, where I think I made a change but it never was processed because I only clicked Save but not Verify (or however it works, I can’t even remember). I have been buying domains for 19 years and can’t handle their stupid interface so I can’t imagine how unsophisticated users can deal with it.
Moniker does not even send messages when domains are transferred out, I am sure most people who park their domains are not even aware. Unless Moniker chooses to make them aware, which I doubt they will do. Just Qéd up a unregistry transfer out, costing me a few grand sooner than I wanted, but what the heck. RIP MONIKER
Most likely, the stolen domains were first pushed to another Moniker account; some were moved out to other registrars eventually.
I just noticed now that Moniker.com offers 2 types of extra security at
http://www.moniker.com/domains/domain-security :
Domain MaxLock – $19.99 per domain
Portfolio MaxLock – $124.99 for all your domains
Considering the recent security breach and stolen domains, they should offer these 2 security options for free right now, to stop people from moving to more secure registrars.
Has anyone affected reported the unauthorised access to the police for investigation ?
This would be a criminal offence, under the computer misuse act, in the UK, and the accessing IP is UK based ,..
inetnum: 88.150.178.56 – 88.150.178.63
netname: RSDEDI-FODNDLPB
descr: Dedicated Server Hosting
country: GB
admin-c: RA1415-RIPE
tech-c: RA1415-RIPE
status: ASSIGNED PA
remarks: ABUSE REPORTS: abuse@redstation.com
mnt-by: REDSTATION-MNT
mnt-domains: REDSTATION-MNT
mnt-routes: REDSTATION-MNT
source: RIPE # Filtered
role: Redstation Admin Role
address: Redstation Limited
address: 2 Frater Gate Business Park
address: Aerodrome Road
address: Gosport
address: Hampshire
address: PO13 0GW
address: UNITED KINGDOM
abuse-mailbox: abuse@redstation.com
admin-c: KMAC-RIPE
tech-c: SL9817-RIPE
nic-hdl: RA1415-RIPE
mnt-by: REDSTATION-MNT
source: RIPE # Filtered
% Information related to ‘88.150.176.0/22AS35662’
route: 88.150.176.0/22
descr: Redstation Limited
origin: AS35662
mnt-by: REDSTATION-MNT
source: RIPE # Filtered
I’ve ranted at Namepros.com about this. My email was not breached. Nor was my password for Moniker, at least on my end. This is a breach at Moniker…plain and simple. They are inept, incompetent, and even worse…negligent. My account compromised on August 27 and I warned them. I tried to have them properly investigate. They just ignored and dismissed me even though I clearly told them what happened and likely how it happened. Instead they responded to me that my email must have been compromised which was utter and complete nonsense.
My account might have been the first account compromised then the exploit was sold or shared and they waited until they have scripts ready to grab as many domains at one time as possible.
And I had portfolio maxlock. Which imho they should refund. I’ve already moved every domain I have away from them. Just in time too.